LinkedIn's war on browser extensions
Posted on Nov 14, 2019
How it all started
You have most likely heard dozens of stories about LinkedIn restricting or banning user accounts due to the use of browser extensions such as email finders or data miners. It's not an understatement to say people are terrified about using extensions on LinkedIn, and for good reason.
Many people have raised such concerns with us, and everyone wants to know what makes Nymeria different. This post serves as a response to those concerns. We also want to publicly share how LinkedIn detects browser extensions and what Nymeria does differently.
How does LinkedIn detect browser extensions?
When visiting LinkedIn your browser will periodically fetch data from LinkedIn's server and store that data in your browser. The data retrieved from LinkedIn is essentially a very large list of browser extension features. The specific data can be categorized in two ways. Each represents a different method used by LinkedIn to detect browser extensions and they are described below.
Method 1) Public Resources
A public resource is any kind of asset the extension uses that is built within the extension and made publicly accessible, such as a logo or icon image.
You can identify all web accessible resources via the extension's manifest file. An easy way to find this list is to use the extension tool CRXCavator and look for the "web_accessible_resources" section of the manifest.
Here's an example taken from Hunter's manifest file:
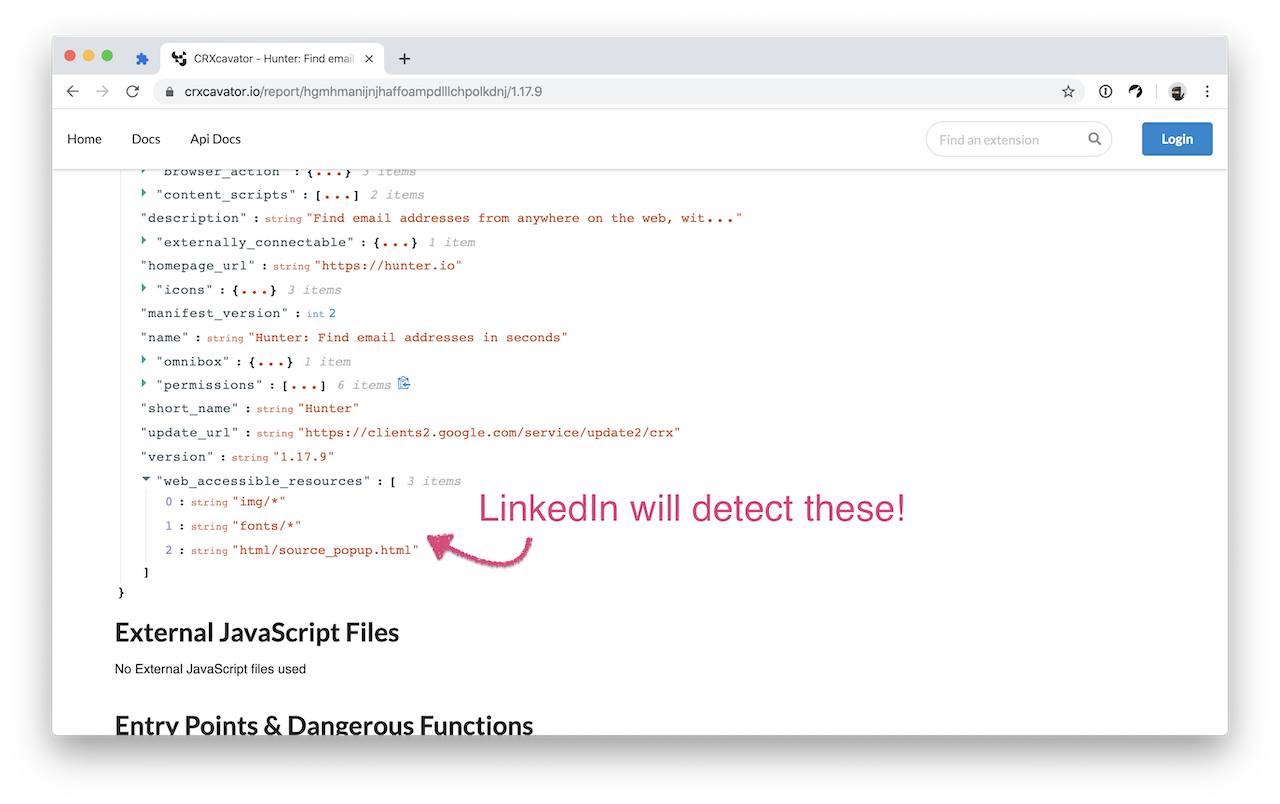
Keep in mind, LinkedIn will detect these even if you don't use the extension on LinkedIn! Simply having the extension installed will put your LinkedIn account at risk.
Method 2) Behavioural Changes
Some browser extensions modify, enhance or change the appearance or structure of a web page. You have probably all seen it, an extension that adds a new button to LinkedIn or adds new functionality to the site. Those are changes in LinkedIn's behavior and unfortunately LinkedIn can detect any changes to its behavior.
LinkedIn keeps a large list of behavioral traits related to different extensions and LinkedIn looks for those changes. If the changes are detected then LinkedIn will know which extensions you are using (and potentially restrict or ban your account).
As an example, the Source Breaker extension adds a window to each LinkedIn profile. The image below is the actual data LinkedIn stores about the Source Breaker extension. It is very clear LinkedIn is actively looking for the window created by the extension.
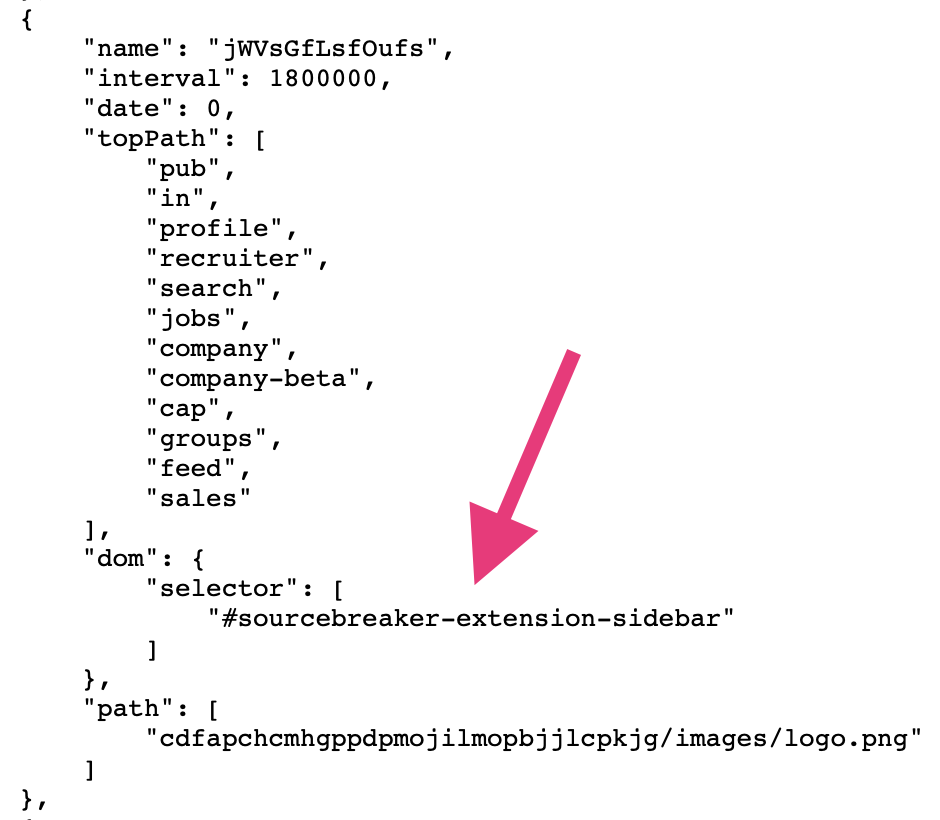
Which browser extensions are currently detected by LinkedIn
At this time LinkedIn is currently scanning your web browser for at least 100 different browser extensions. If you have installed any of the following extensions your account is at risk:
- Adapt Prospector
- Adorito
- AeroLeads
- Aevy
- Alfred
- Alore.io
- Amazinghiring
- Auto Connect Tools Lily
- Candidate.Ai
- CleverStaff
- Colabo Extension
- Contact Out
- Crelate
- Data Scraper
- Datananas
- Daxtra
- Discoverly
- Dux Soup
- E-Reveal
- Ebstabullhorn
- EbstaSalesforce
- Ecquire
- ELink Pro
- Email Finder
- Email Hunter
- Emply
- Entelo
- EyeMail
- Find That Lead
- Found.Ly
- Gem
- Get Email
- Hiretual
- HR-Skyen
- Icebreaker
- iMacros
- Instant Data Scraper
- Jaspr
- Jlenty
- Lead Generator
- LeadConnect
- LeadGibbon
- LeadIQ
- Leadkedin
- Leadzippo
- Leonard For Linkedin
- Linked Helper
- LinkedAssist
- Linkedbot
- LinkedHub 1.0
- LinkedHub 2.0
- Linkedin Assistant Lily
- Linkedin-Hubspot Connector
- LinkedPro
- Linkedroid
- LinkeLead
- LinkGenius
- Linklead.io
- LinkMatch For CatS
- LinkMatch For Greenhouse
- LinkMatch For PCrecruiter
- LinkMatch For Pipedrive
- LinkMatch For Zoho CrM
- LinkMatch For Zoho Recruit
- LinkMe Tool
- LinMailNavigator
- LinMailPro
- Livehive
- Loxo Social Import
- Lusha
- Manatal
- Nimble
- OctopusCRM
- People Finder
- People.Camp
- Private Notes For Linkedin
- Prophet
- Prospect.io
- ProspectHive
- Prospectify
- Ramper
- RecruiterNerd
- Resource
- Sales Lead Multiplier
- Saleslift.io
- SalesLoftCadence
- SalesloftProspector
- Salestools
- SeekOut
- SellHack
- Skrapp
- Slik
- Snapaddy Grabber
- Social Lead Machine
- Social2Sugar
- Socialbff
- Sourcebreaker
- Sourcehub
- Spider For Linkedin
- StepWells (Colabo)
- Talentbin
- TazzHr
- TurboHiring
- UltraScrapper
Last year there were a mere 40 extensions and now the list is over a hundred extensions and growing. Be careful which extensions you install and keep public resources and page changes in mind when selecting which extensions to install.
What does Nymeria do differently?
One of the great advantages of browser extensions is the ability to modify web pages and add missing or desired functionality. In order to prevent detection from a site such as LinkedIn, the Nymeria extension does not modify any web page you visit. This is great for your privacy but unfortunate because the Nymeria extension is not able to enhance any pages you visit.
Instead, Nymeria uses a "browser action", which is a browser extension pop-up window to display Nymeria's content. This is less convenient than modifying a website's page, but isolates the extension and prevents websites from detecting the usage of an extension.
Furthermore, Nymeria does not expose any public resources through the extension and cannot be detected through such methods. We are always on the look out for new and better ways to prevent detection and keep our users safe.
We hope you found this interesting. If you have any comments or questions, shoot us an email!
Want to try for free?
Leverage Nymeria to quickly and easily find fresh email and phone data for your business.